Many of us who work in the software security field even need to do a “security healthcheck” from time-to-time. For me, my data security also includes privacy. After all, if my data is being sent to every Tom, Dick, and Harry, then the chances that it gets into the wrong hands or hands with improper security implementations increases astronomically.
In fact, I’ve noticed a parallel with data privacy and performance as well – apps which are logging and sending your every move behind your back also introduce bloat in RAM, waste internet bandwidth, and have reliability issues such as when one of the 1,000 third party libraries and “services” they use to track you crashes.
For the above reasons, locking down your workstation can take some time, but trust me, it’s well worth it.
Today, I will cover several topics:
1.) Password Managers
2.) Browser Privacy
3.) Sandboxing/Virtualization
4.) Background processes/services/daemons
By implementing these 4 things properly into your workflow, you can greatly increase your level of operational security and protect the privacy of you and your loved ones.
Password Manager
Password Managers may seem like a bad idea. They operate off of the principle of trading the nuisance of dealing with tens or hundreds of passwords for the nuisance of dealing with just 1 very good password. Let’s think about this for a second – One very good password is demonstrated to take up to billions of years to crack with modern computing power. This means that a strong password is actually very effective so long as there is no side-channel attack involved. A side-channel attack could be you downloading malware and the malware captures the password as you type it in. This is not technically a “password crack” but rather, the mistake led to your password being leaked out. This is much different from a computer trying millions and billions of attempts on your password and actually discovering (cracking) it.
When implemented properly, a password manager will store your passwords in an encrypted form at all times. What does “all times” mean?
1.) In memory on the local machine from which it is being accessed or written to
2.) In transit to any type of cloud or shared service
3.) On-disk on the local machine or cloud/shared service
Modern password manager applications accomplish this. In fact, if the password manager follows a secure design and implementation, even if it is “breached”, malicious actors will still not be able to get your passwords. Technologies such as end-to-end encryption are used so that if the password manager’s server is compromised, the attacker will be able to read a whole bunch of encrypted passwords which make no sense to him/her.
Browser Privacy
Let’s talk about browsing. Most of us spend the majority of a time in a web browser due to the large number of websites and web apps that exist. This effectively means that the web browser is almost like a full operating system in and of itself – it communicates via the network, it runs programs and applications, it plays multimedia, it is a native process which has access to the host operating system, and most importantly, it accepts, receives, and transmits most of our sensitive data.
Web mail programs such as gmail, Yahoo mail, protonmail, and more are used to access email which is in turn used to reset passwords, perform 2 factor authentication, view bank receipts and package tracking data, and etc… All within the web browser. What’s more? The browser platforms provide an extension or add-on system which allows users to download and install nearly an unlimited number of plugins, which are in turn allowed to access user data, and are developed by various 3rd parties whom the user doesn’t know. Sounds like a nightmare fraught with risk. This is the modern web. Yet, relatively few users are willing to spend some time considering their browser’s privacy and security health, settings, and posture.
The good part is that taking action to greatly increase your web browsing experience is becoming easier and far less time consuming. Let’s discuss several key subpoints:
A) Secure Email – Gmail – Google views all of your emails
B) Analytics/Tracking – redmorph, duckduckgo anti tracking also saves bandwith
C) Credential stores – Saving passwords and credit cards
D) Browser extensions and plugins – Know what they’re doing… Also, utilize the good ones!
Secure/Private Email
Gmail and similar services owned by large social media conglomerates are offered “free.” As the saying goes, “nothing in life is free.” This is true here as well. They do this because their software views all of your email and stores data about who emails you, the content of the email, the subjects, etc… This allows Google to “offer you a more personalized experience” as they put it. What it really means is that they learn about you as a person and can sell tailored advertisements to you based upon your interests. I don’t know about you but very rarely if ever, do I actually end up making a purchase from a web ad alone… In fact, typically I would Google search for a product such as a new pair of headphones and do a bunch of research. I would then purchase the headphones, and then the week after my purchase, see a bunch of ads for the same or similar headphones. This was not very useful and not at all worth some company storing a bunch of data on me. However, they use this “tailored experience” argument to continue getting away with tracking your every move.
It’s one of those things where you don’t realize how useless it is until you step out of it for a while and either miss nothing or even enjoy life more online. Try it.
DuckDuckGo lists emails which do not engage in this behavior here. Probably the most well-known one is ProtonMail. I’ve noted that several of these are not just very secure, but they allow for totally anonymous setup by not requiring a full name, not storing machine data when the email is registered, and accepting payment via cryptocurrency. Additionally, services such as NeoMailbox and ProtonMail are “offshore” in Switzerland and other countries with strict privacy laws. The idea here is that it is also harder to get a legal subpoena on these services in an investigation, etc… It’s true that these services can also be used by folks doing illegal activity, but there are happy mediums such as FastMail which just generally has a “respect your privacy” model but without the total anonymous registration and offshore servers. Up to you.
Cost
Expect to pay around $5/month for these services, as again, “nothing in life is (truly) free.” I’m ok with this.
Private email caveat
It’s worth mentioning – don’t forget email is a 2+ way communication method. This means that depending on the content of the email, you should be aware that whomever you send it to will also get a stored copy. So it’s not super useful to De-Gmail your life if you’re sending 90% of your emails to Gmail users. Why? Because Google will still see them in the recipient’s mailbox, and there’s nothing you can do about that. 🙂 So if you don’t want particular email to be read/analyzed by Google, then don’t send that message to a Gmail user, etc…
Analytics/Tracking
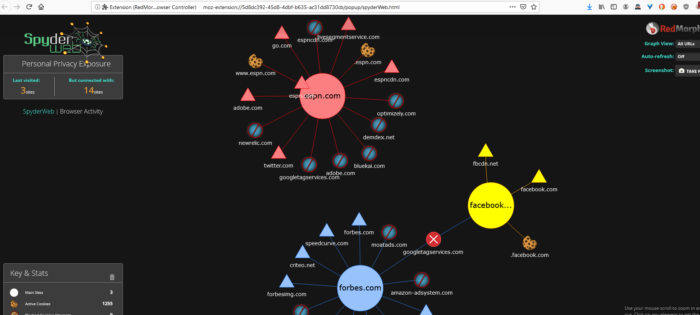
The next pillar in this discussion involves analytics. We touched on it before but essentially, websites will send your information to thousands of 3rd parties as soon as you visit them. Nearly all websites do this now adays. This uses bandwidth, slows the websites down, eats up RAM, discloses your private browsing habits and data, and can also cause site reliability issues. The simple solution to this is to use a browser with “Content Blocking” or Tracker Blocking such as Firefox or Brave with mode set to “Strict” or use a browser plugin such as Redmorph, DuckDuckGo, or other “tracker blocking” plugins. Here is a screenshot of something Redmorph calls the “Spyder Web” of all of the tracking services that a webpage tried to send my data out to – it’s alarming and creepy!
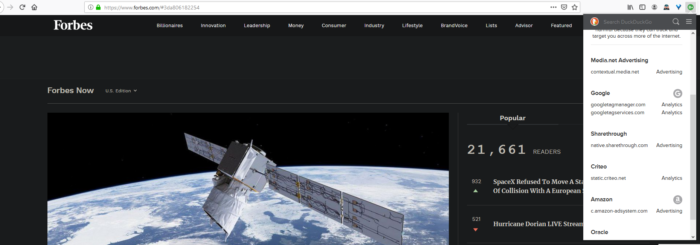
And here’s a partial list of blocked trackers from Forbes.com, a tracking nightmare of a website:
Credential Stores
Browser Credential Stores are the option where the browser asks if you want to save or remember a password so that when you visit the login page next time, it is auto-filled for you. This is different from checking a “remember me” tickbox on a website, which just increases the length of your session tokens/cookies so that you actually stay logged into the website for a longer period of time before being logged out.
Long story short: these browser credential stores pose a significant security risk because they expose passwords to anyone on your machine. For example say you forget to lock your computer before walking away from it. Yes, this is pretty bad already, but in reality, it’s possible for example, that even in this situation, an attacker with physical access to your machine, still is unable to access your bank account.
Most banks enforce a very strict session duration so that if the user hasn’t made an action on their website in about 5 minutes, the session expires and the user is logged out. If the user has not chosen the option to remember his/her password in their browser, then someone who has access to the machine may not be able to login to the bank account.
On the other hand, if the password is stored in the browser, now anyone with access to the machine can access the bank account, and unless the user has set a “master password” in his/her web browser, the attacker can also view the passwords by opening the browser and going to the password settings. Not good.
So once again, the “remember password” feature of browsers is a battle of convenience vs security. In this regard, I choose to let my Password Manager handle the passwords because the password manager, like the bank website, will auto logout after a couple minutes and if someone is able to get onto my machine, they will need to know my master password to get into any of my accounts.
Browser Extensions & Plugins
Much like background processes on a computer or mobile device, browser extensions and plugins often have access to view and sometimes even modify anything that is happening inside the browser. What this means is that even if the browser itself is locked down, and running in a virtual machine with limited privileges and access, if a shady browser extension is running, it could be sending your personal data to third party tracking networks, or even serve as a total backdoor, sending your entered passwords to a server. For this reason, and to limit system resource usage, it is important to use as few extensions as possible and make sure that they come from trustworthy sources.
Sandboxing & Virtualization

So what if one of those applications above fails to do its duty, the developer is actually malicious, or you accidentally download and run some malicious app? That is where sandboxing and virtualization come in! Luckily, applications only have access to the environment they are installed on (the operating system) and any connected peripheral devices (including wireless networks if applicable). What this means is that a malicious app cannot access data on a computer in another room which is not hooked up to a network. Luckily, with modern virtual machine software (hypervisors) such as VMWare and VirtualBox, software isolation is possible so that a compromised app cannot infect other vital assets on the machine.
Simply put, a virtual machine emulates an actual computer, and it has the effect of:
A) Being a “computer in a window” – You the user literally see another PC complete with a desktop, taskbar, drives, ports, etc in a window on your main machine
B) Anything that happens in that “PC in a Window” stays in there**. This means that instead of installing instant messaging apps, random tools, Adobe and other software you use in your day-to-day workflow on your actual computer, you fire up this virtual machine (VM) and install that software in there. That way, if the software corrupts your computer in any way such as damaging the registry, installing adware, installing malware, or just hogging system resources (like having 10 background “services” running), you aren’t actually bogging down your computer. Instead, you are bogging down the virtual machine which can be restored or wiped out much more easily.
The other huge benefit of installing software into a virtual machine for privacy is that it only has access to the environment in that virtual machine. So for example, say you have 1 virtual machine you use for surfing the web and chatting with your friends. You can use another virtual machine in which all you do is your banking and purchasing. This way, if you install some malware or spyware (including Google’s spyware) on the surfing machine, it cannot see anything you do on your banking machine, and vice versa.
**NOTE: The statement above does not account for so-called “VM Escape” security vulnerabilities. It is possible, but extremely unlikely, that a Virtual Machine platform such as VMWare or VirtualBox will have a vulnerability allowing malware to escape from a virtual machine to the host machine. People who hear of using VMs for security or privacy reasons will often cry about this but fail to realize how rare it is. A VM Escape vuln is literally worth hundreds of thousands if not several million dollars on the 0-day exploit market because it would be able to be deployed against cloud services, government, etc… So the likelihood that if someone has a VM escape vulnerability, they would use it on your VM is very low unless you are a very high profile individual or get caught up in some extremely rare malware infection case. There are literally people who spend all day every day running hundreds of malwares in VMs who have never encountered a VM escape. Saying you should not use a VM because of a VM escape vuln is like saying you should never drive anywhere because of car accidents.
Onboarding the workflow
Truth be told, the workflow will take a day or two to get used to, but if you have a capable machine (I’d recommend at least 32GB of RAM and a modern Ryzen processor), it’s totally worth the security benefits. Even still, the initial effect will be slightly more complex than using only your main PC without virtual machines, especially if you do not have multiple monitors. However, the payoff will be great a few months down the road because your main PC (aka “host”) will be completely free of crap and you won’t be a slave to Google, Facebook, and their 1,000s of tracking networks. The added benefit here is also reduced bandwidth usage which adds up fast. Meaning, if you go to for example https://espn.com , before, your browser made maybe 100 calls to trackers per page… Now, it only makes the calls necessary to load the page so the number of outbound requests is greatly reduced and thus data transfer is reduced.
Background Processes/Services/Daemons
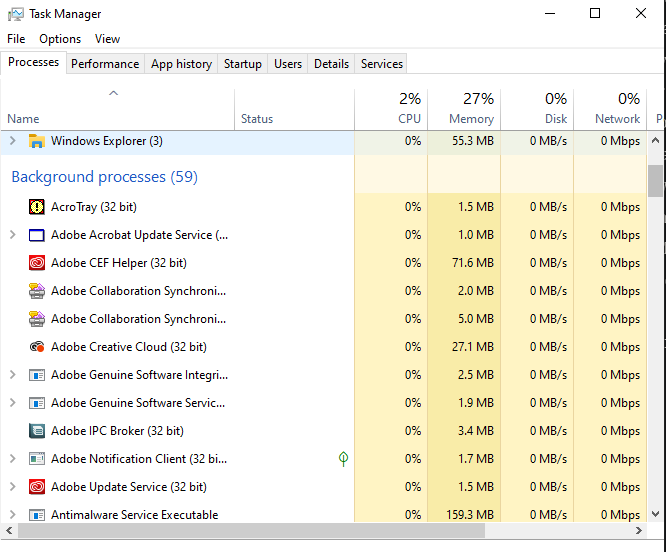
Last but definitely not least, a good practice is to be aware of the hundreds of background processes running on modern desktops & laptops, and the dozens running on mobile devices. In fact, I feel that this may be the most overlooked area of computer security. Background processes often are granted access to a lot of information entered into the machine by the user, in the Windows registry, filesystem, etc… Many even have access to the system clipboard where sensitive data is copied/pasted. It’s very easy to overlook just one malicious process or process which may be leaking your sensitive data. We rely on computer antimalware but unfortunately, some background tracking processes are not considered to be “malware” because the user agreed to be tracked in some huge EULA that they did not read. For this reason, it’s good to follow a policy of eliminating as many background processes as possible. For example, Google Chrome browser on my machine installed 3 services shown below:
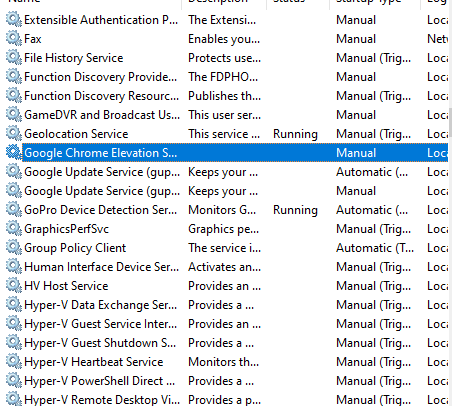
The thing is, I have no clue what these services are really doing. Sure, they say that they are only monitoring for updates and such, but if I know Google, they’re also sending some analytic data out… At some point, you just develop “security common sense,” which basically means that you assume any process could potentially be giving away your private data. For me, this meant that I removed Google Chrome and installed Firefox, which only has 1 update service instead of 3. Also, Firefox does still send out analytic data, but they market themselves as a privacy-aware service and have a decent reputation as such, so I’m willing to bet that Firefox’s service is a safer bet than Google’s 3 services. To access these services, by the way, you can press the Windows key and type in Services and hit enter on Windows.
For macOS, you can use the built-in Activity Monitor to view much of the same information (hit cmd+enter and type in Activity Monitor). Also, there is the little-known FireEye Monitor.app which is similar to Windows Sysinternals Process Monitor – it provides detailed logs on all running process activity. Note that on Unix-based platforms, “services” are typically called daemons. On Linux, the “ps” terminal command can be used to view all processes loaded in memory. The Tl;Dr here is know the background processes running on your machine.
On Windows, there is a useful suite of tools called Sysinternals and a particular program called Process Explorer which can aid here – once you run it, you can specify to “verify signer” which shows whether or not a processs is signed. You can also specify to submit processes to VirusTotal as an added malware check. But again, many processes sending out your personal data are not going to be flagged as malware. One technique that I’ve used to keep track of all of this is viewing the process list right after I’ve performed a fresh OS install without bloatware (meaning, I installed the OS myself, did not rely on the PC manufacturer’s install which may come with so-called “bloatware” which may be sending your personal data out from the very beginning!
Finally, the virtualization recommendation helps a lot here – processes will only be able to see what is on that virtual machine. For example, I have Adobe Creative Cloud installed in a virtual machine and Adobe has numerous background processes and services running which do not have access to anything I do on my host or other virtual machines.
Conclusion
In the end, the security of you and your family’s data is only as good as the effort you put into it. Much like watering plants, taking care of pets, and organizing your dwelling, data security is another area of your life that you must prioritize, research, and spend some maintenance time on. Problems arise for those who choose to neglect it or stay misinformed and then suddenly realize they’ve had their data compromised or accounts stolen. Additionally, maybe neither of those two things occur, but devices get slowed down and bandwidth is wasted on all of these free “services” which are selling your browsing habits and computer activity. Either way, security and privacy need to be addressed but not all of these araes need to be addressed at once. Instead of becoming paranoid or overwhelmed, an iterative approach of transitioning even just one of two of these areas is very helpful and has become much easier with tools like DuckDuckGo, ProtonMail, virtual machines, process monitoring, and etc…

