If you view a PE file’s function imports, you may sometimes come across a bunch of nondescript numbers like so:
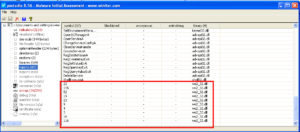
These are simply function ordinals, which are ID numbers to Windows API function calls… In this case, we’re looking at Ws2_32.dll which houses Winsock functions. So, in a nutshell, these are socket create/connect/send/receive calls which means that this malware is likely using networking/the Internet. There are several reasons why a programmer may use ordinals instead of function names. It is quicker because the loader doesn’t need to use a lookup table to resolve the names at runtime, and it also, as you see here, keeps function names out of the file which can make it more difficult to analyze. Luckily, once you recognize these as being ordinals for a particular DLL, you can begin your search to find out the function names. This link shows us that we’re dealing with:
- shutdown
- gethostbyname
- WSAStartup
- send
- socket
- htons
- connect
- recv
There are a few others there, but those are all we need to get a glimpse into what this malware is doing on the network side of things. While this certainly doesn’t conclude our investigation, any intel helps. So next time you see dll imports with just integers like that, do a search for ordinals on that particular DLL to shed some light.
If you are not familiar with the above functions, I recommend Beej’s Guide to Network Programming. He explains all of these functions. The tutorial is Linux-focused, but you’ll definitely get the idea as most functions are implemented on both OSes.
