I wanted to mention a tool that I’ve found very helpful in analyzing Portable Executable (PE) files: PortEx Analyzer by Karsten Hahn. Actually, the first very noticeable difference between this program and so many others is the level of documentation. PortEx Analyzer is fully documented by Hahn and has a thorough readme and wiki as well. 60%+ of the time that I’ve viewed open source projects on GitHub, this is not the case which can actually impact the usability of the software, so kudos to Karsten for that right off the start!
PortEx Analyzer has a lot of capability – far more than I’ve used, but sometimes the simple usages of a program are equally as important as the more complex ones. My favorite part is that PortEx creates a nice visualization of file entropy, exportable to an image file as well as a logfile of all of its findings. It is also up to date and maintained by Karsten. The entropy images allow for easy detection of compression and encryption in specific areas of files or the entire file, see the sample:
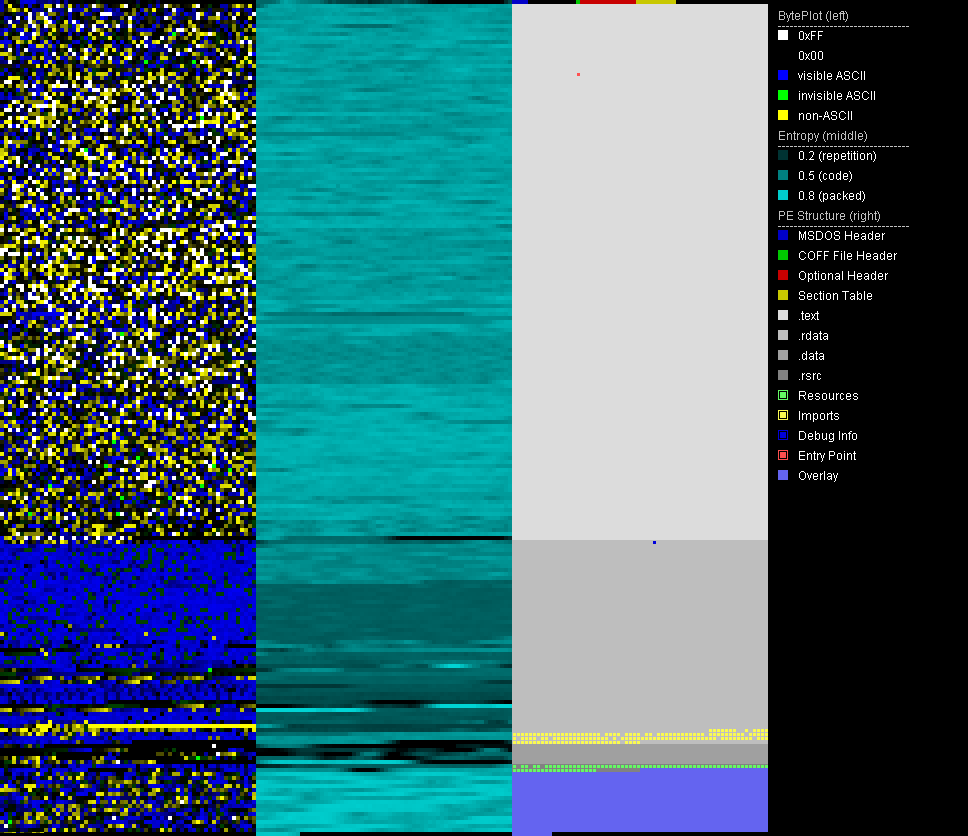
The legend on the right side of the output is self-explanatory, but the real magic of the tool can be seen when comparing several of these images side by side… Such as one which represents a packed/compressed executable and an uncompressed one.
PortEx Analyzer also parses typical portable executable format information such as header information, sections, directories, and hashes, similar to PE Studio. One highlight of PortEx is that it logs the RVA and estimated VA of each import as well as the DLL’s Export Table hint indices. If you are not familiar with the hint, it is optionally used to speed up an external function name lookup. When a DLL is imported into a program (such as Kernel32.dll) and a function is called by name, there is a lookup process where the name has to be found in a the DLL’s Export Address Table. This process can be shortened with the help of the hint which allows for an instant lookup within the array rather than having to do for example, a binary search for the function name. So the hint tells us where in the DLL’s Export Address Table the function is. This process is also sped up when a function is called by Ordinal rather than name, so no name lookup is necessary.
PortEx Analyzer provides short descriptions of known API imports as well as PEiD results and suspicious findings. An example listing of import API functions:
ADVAPI32.dll
————
[Registry] <Obsolete>
rva: 0x2efac, va: 0x42efa0, hint: 607, name: RegOpenKeyA -> no description
rva: 0x2efb0, va: 0x42efa0, hint: 567, name: RegCreateKeyA -> no description[Registry]
rva: 0x2efa0, va: 0x42efa0, hint: 622, name: RegQueryValueExW -> Retrieves the type and data for a specified value name associated with an open registry key.
rva: 0x2efa4, va: 0x42efa0, hint: 621, name: RegQueryValueExA -> Retrieves the type and data for a specified value name associated with an open registry key.
rva: 0x2efa8, va: 0x42efa0, hint: 608, name: RegOpenKeyExA -> Opens the specified registry key.
rva: 0x2efb4, va: 0x42efa0, hint: 560, name: RegCloseKey -> Closes a handle to the specified registry key.
rva: 0x2efb8, va: 0x42efa0, hint: 637, name: RegSetValueExA -> Sets the data and type of a specified value under a registry key.
The imports are organized by DLL file.
And more info:
Anomalies
********** Optional Header: size of initialized data is too large (0x10400), it should be 0xe600
* Import function typical for code injection: LoadLibraryA maps module into the address space of the calling processPEID Signatures
***************[Microsoft Visual C++ v8.0] bytes matched: 4 at address: 0x490b
pattern: e8 ?? ?? ?? ?? e9 ?? ?? ff ff
The official list of features:
- Reading header information from: MSDOS Header, COFF File Header, Optional Header, Section Table
- Reading standard section formats: Import Section, Resource Section, Export Section, Debug Section, Relocations
- Dumping of sections, overlay, embedded ZIP, JAR or .class files
- Scanning for file anomalies, including structural anomalies, deprecated, reserved, wrong or non-default values.
- Visualize a PE file structure as it is on disk and visualize the local entropies of the file
- Calculate Shannon Entropy for files and sections
- Calculate hash values for files and sections
- Scan for PEiD signatures or your own signature database
- Scan for Jar to EXE wrapper (e.g. exe4j, jsmooth, jar2exe, launch4j)
- Extract Unicode and ASCII strings contained in the file
- Overlay detection and dumping
- Extraction of ICO files from resource section
- Extraction of version information from the file
Head on over and check it out. You will see more posts utilizing this tool and we will explore its capabilities further in context. Last but not least, if you want to learn more about the how and why behind PortEx, as well as learn more about Malware Analysis in general, I highly recommend giving Hahn’s master thesis a read. I read it and learned a great deal not just about the implementation of PortEx but about malware as well.
